Tenvis JPT3815W: A cheap network camera, if you can afford the huge security issues
30 June 2014

I recently purchased a cheap, Chinese network PTZ camera which comes under the branding “Tenvis”. It set my wallet back by 50€, including shipping from the UK. I decided to get this one, after reading some positive reviews which labeled it as a great value for money option. Additionally, I saw that “Tenvis” had a real website and an English forum, so I thought “why not”.
Generally, it’s a satisfactory camera for its price, setup is really fast, just finding the camera’s IP and you are ready to go. Also, they provide a unique link to it, through their dynamic DNS service, so you can access it remotely without having to worry about the various local IP changes. You just need to enter your username and your password (you can also create new users with various permissions) to gain access. I also need to mention that my camera came with “Hardware Version 1.10” and “Firmware Version 1.1.0.5”.
However, there’s a darker side to all this. As with many Chinese products, documentation and support is really poor. First, I realized, that their web client for non-IE browsers (who uses IE these days anyway?!), does not support audio in and audio out from the camera, which is within the camera’s specifications. This is very inconvenient, especially for my case that I wanted to monitor the feed from these cameras using a Raspberry Pi. In other words, no Windows and no Internet Explorer. Since their Android app seemed to support the audio features (haven’t actually managed to successfully send audio to the camera from the android client yet though) I justifiably assumed that there should be an API for all this and so I inquired for one, at their support email and forums. Sadly enough, I just received an answer that there is no API, however there’s an SDK for my model instead to which they provided a link for. Fair enough. Long story short, after fiddling around with it, I didn’t manage to get most functionalities described in the SDK working, so no sound thus far. To my great surprise, some of the functions did work, but not as described and not really as… expected.
More specifically in their SDK, they provide a snapshot function. You type in the camera’s address, open the snapshot interface (snapshot.cgi), provide in the request your username and password and you eventually get a still from what the camera is filming at that moment. They claim a security level of “visitor” and above can access it. (There are three total types of users, the “administrators”, the “operators” and the “visitors”.)
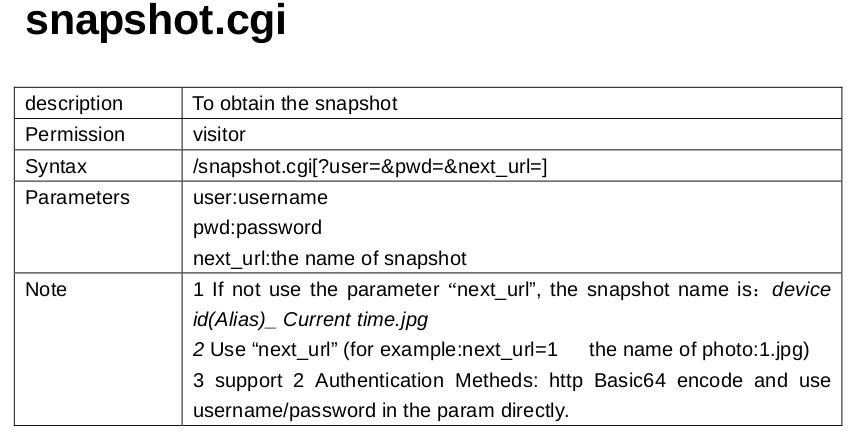
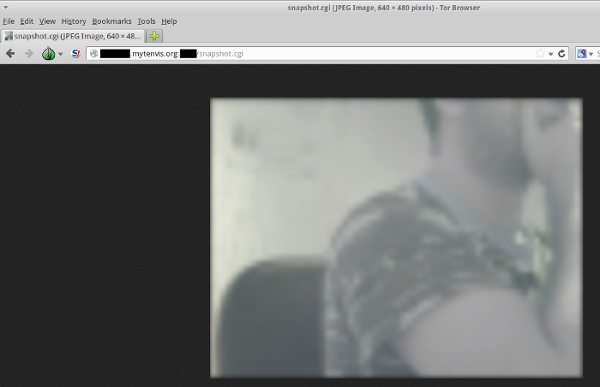
Makes sense. Well, what doesn’t is that I consecutively discovered that entering your username and password is entirely optional, resulting in ANYONE being able to watch that snapshot. And of course if someone can get a snapshot, they can get a series of snapshots or more commonly known as an MJPEG video stream. To put it differently, EVERYONE who has just the link to your camera can watch its live feed. Good bye privacy! Considering that all connections to the camera are through HTTP plain text connection, it is relatively easy for the attacker to find the camera’s address. The following screenshot is made from a TOR browser, no cookies, no previous logins whatsoever. The camera’s link is darked out because I don’t want you guys checking out my house, thanks to Tenvis…
To make matters worse, while digging deeper in the SDK, trying to get something meaningful (i.e. the sound) working, I discovered an even larger and much more serious security hole. The SDK provides a function to obtain the device settings info (sic). Only the administrators can have access to it according to the documentation.
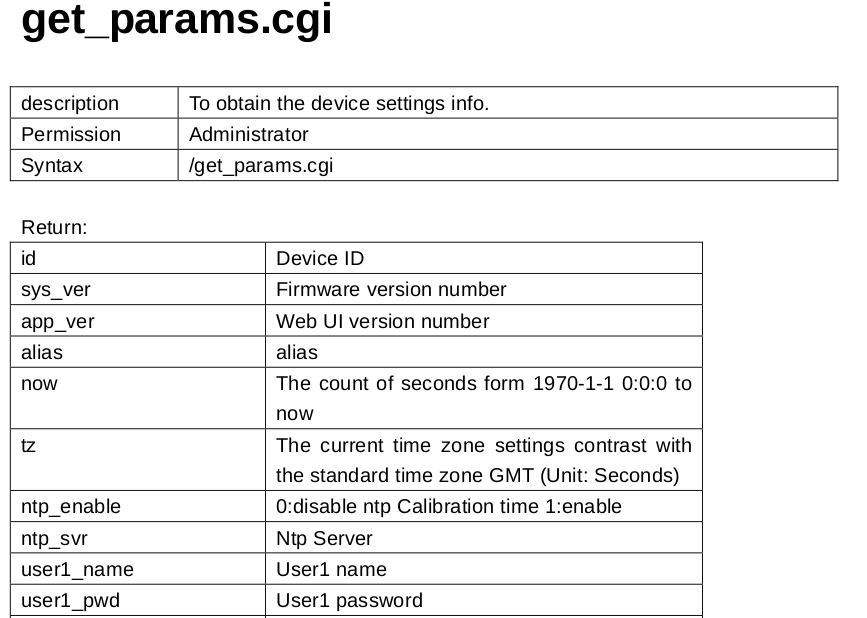
As you might have guessed by now, that is not true. In fact ANYONE can have access to this information. Want to have a look what that might be? Here you go:
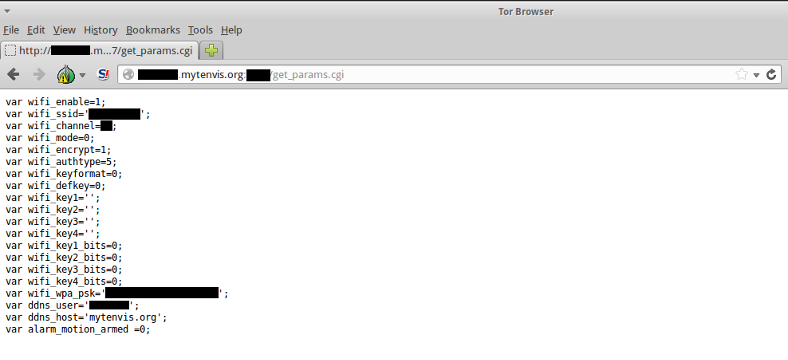
Oh Yes! My local wifi’s SSID and its so precious and non mnemonic password, all exposed to the public eye. That was a bit of a shock to me, which resulted in avoiding to leave the camera on for long periods of time. But wait, isn’t that the purpose of the network camera?
Generally, I have read that these “security cameras interfaces” are generally far from secure, but still, I think this is too much. I have contacted Tenvis, with this information expressing my disappointment and currently waiting for their reply. For others who are on the lookout for buying a network camera or are considering to buy this one, keep these things in mind. It is unsafe and you will have a hard time using all of its functionalities without an Internet Explorer. That is, until at least they patch these serious bugs. UPDATE: Tenvis replied to my email, in which I was expressing my dissatisfaction as well as exposing the security threat:
Dear Customer,
Greetings from TENVIS!
This is Bruce from TENVIS custom service. We are very pleased to assist you to solve the problem. We guess you are an IT guy. I’m afraid at present, we have no better way to protect customer’s privacy. Hope you can understand our difficulty.
If you have further questions, please feel free to contact us. Thanks.
Have a nice day!
Best Regards
I was personally rather surprised by their answer and complete reluctance to take this more seriously. I guess I did everything I could, but now they have a very dangerous live exploit in their products.

